Before you start
You need to create a new application in Auth0 Dashboard or convert an existing application before you continue. To learn more, read Configure Private Key JWT Authentication.
private_key_jwt:
- Build the client assertion. This assertion is a JWT signed by the private key when you generated the key pair. To learn how to generate a key pair, read Configure Private Key JWT Authentication.
- Use the assertion to authenticate against Auth0.
Build the assertion
You can use one of Auth0’s SDKs to build an assertion automatically for you. If you don’t use our SDKs, you will need to construct the assertion yourself. The assertion is a (JWT) that should contain the following properties and claims:All claims are required unless otherwise stated. To learn more about JWT claims, read JSON Web Token Claims.
-
Header
alg: The algorithm used to sign the assertion. The algorithm must match the algorithm specified when you created your application credential.kid: (optional) The Auth0 generatedkidof the credential. Thekidis created when you created the credential.
-
Payload
-
iss: Your application’s Client ID. You can find this value in your application settings under Auth0 Dashboard > Applications > Applications and select the Settings tab. -
sub: Your application’s Client ID. You also can find this value in your application settings. You can find this value in your application settings under Auth0 Dashboard > Applications > Applications and select the Settings tab. -
aud: The URL of the Auth0 tenant or custom domain that receives the assertion. For example:https://{yourTenant}.auth0.com/. Include the trailing slash.If you have configured a custom domain for your Auth0 tenant, this can be used as theaudclaim. We recommend using the custom domain in this case. -
iat(optional),nbf(optional), andexp: Issued At, Not Before, and Expiration claims set to the correct timestamps. A clock skew of up to 10 seconds is allowed foriatandnbf(if present) to support inter-operability. The client assertion is a one-time use token, and we recommend the shortest possible expiry time. Auth0 supports a maximum of 5 minutes for the lifetime of a token. -
jti: A unique claim ID created by the client. We recommend using the Universally Unique Identifier (UUID) format.
-
Example
In the example below, the Node.js script uses a jose package to generate the assertion: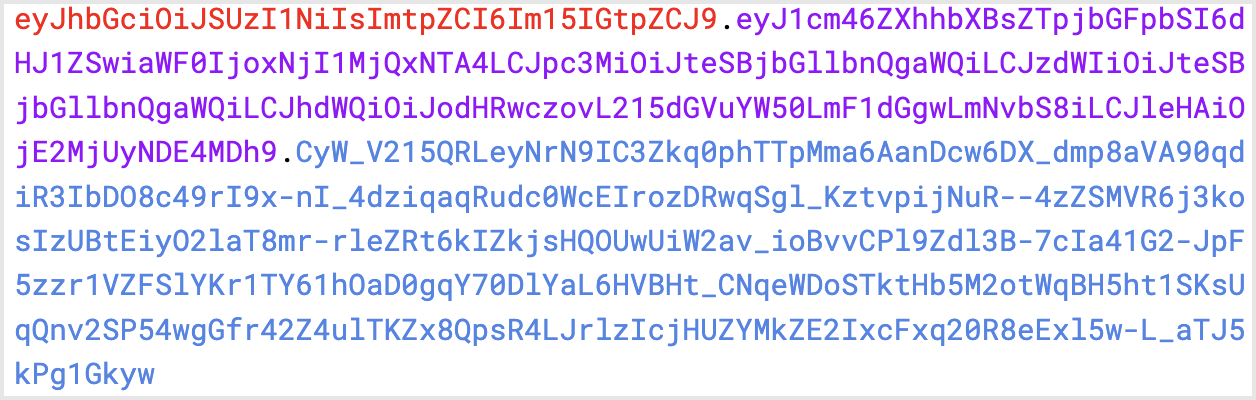
Exchange assertion for access tokens
The following example uses the Client Credential Flow. Private Key JWT authentication can be used for other grant types that also allow replacing
client_secret with client_assertion.$client_assertion: JWT assertion$resource_server_identifier: identifier. To learn more, read Register APIs.
Supported endpoints
In addition to the https://$tenant/oauth/token endpoint, the following Auth0 Authentication API endpoints supportprivate_key_jwt authentication for configured applications:
Assertion limits
The maximum length of the JWT assertion is 2048 bytes. Claims within the assertion have the following limits:iss: 64 characterssub: 64 charactersjti: 64 charactersalg: 16 characters

